Protect your domain name from cache poisoning.
In recent years, hackers have developed methods of ‘poisoning’ DNS servers by falsifying the responses given by the DNS, enabling them to divert traffic to their servers (phishing etc.). With our DNSSEC solution, you can now protect your DNS servers.
DNSSEC
- Secure DNS
- Protection against cache poisoning
Enabled via the OVHcloud Control Panel
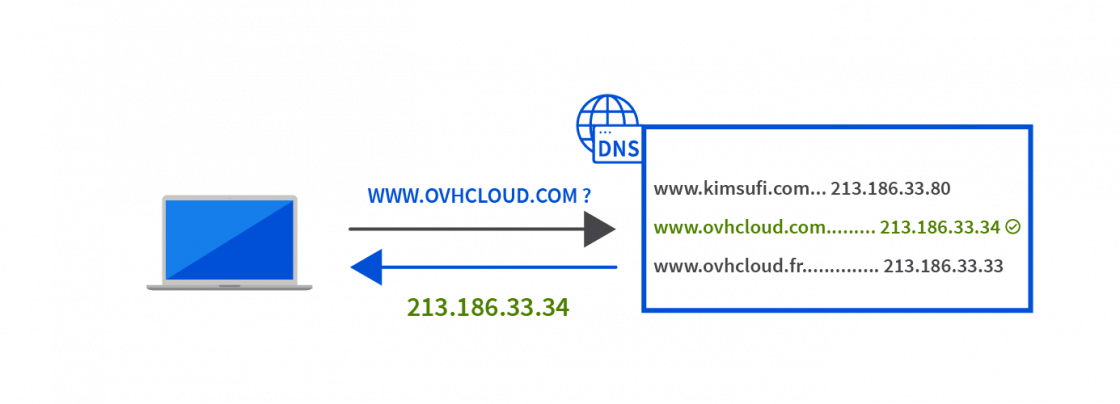
How an attack works and how it is protected by DNSSEC
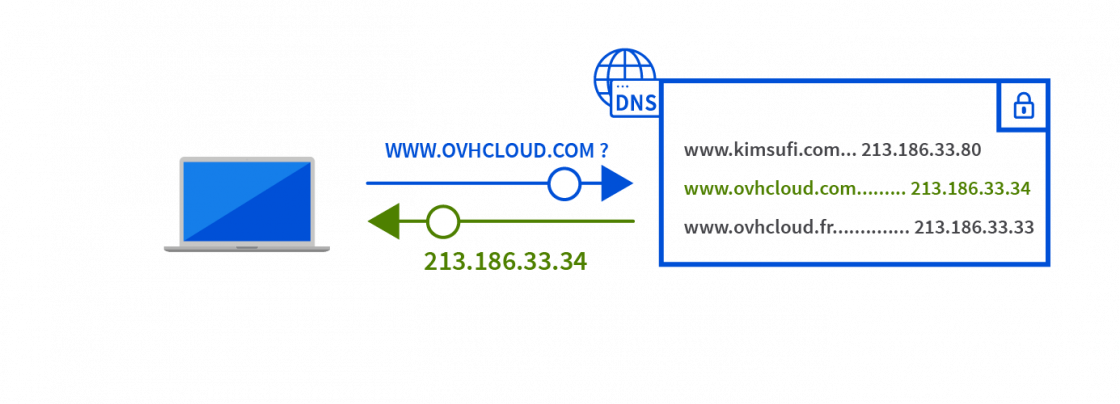
The user enters the address www.ovhcloud.com in their internet browser. A query is then sent to the DNS server, which returns the corresponding IP address: 213.186.33.34.
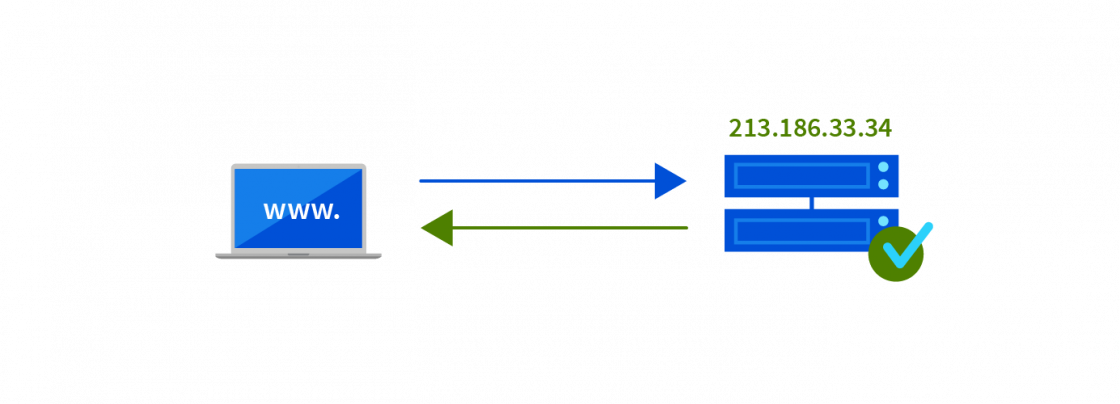
The internet browser now knows the IP address of the server hosting that website. It then sends a query to this IP address, which returns the contents of the page.
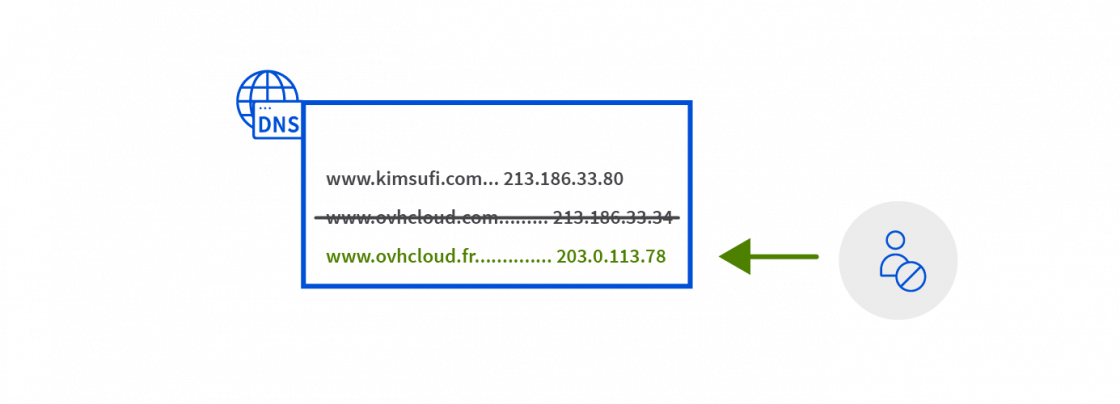
The danger: Cache Poisoning
A hacker has detected a vulnerability in the DNS server. They manage to access the server and modify the address corresponding to www.ovhcloud.com with the IP of a secondary server belonging to them: 203.0.113.78.
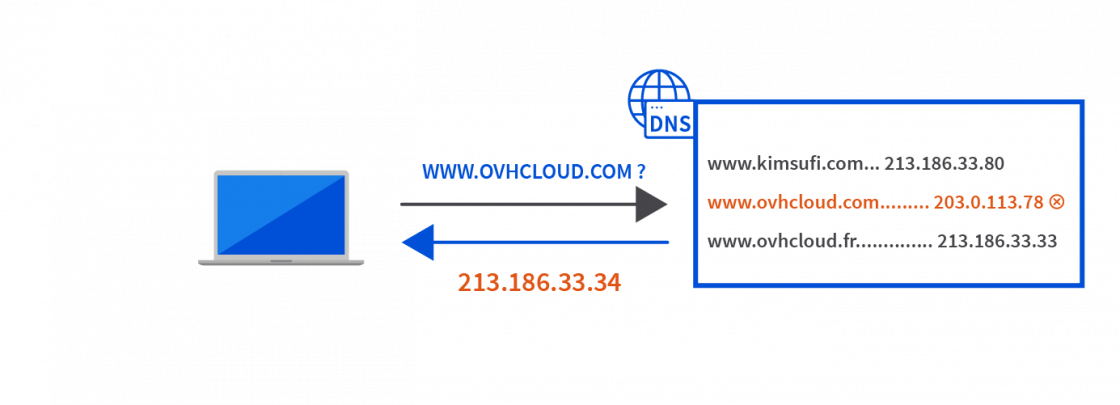
When the user enters the address www.ovhcloud.com, their browser will be directed to the DNS server to retrieve the corresponding IP address. The “poisoned” DNS server gives the IP address inserted by the hacker: 203.0.113.78.
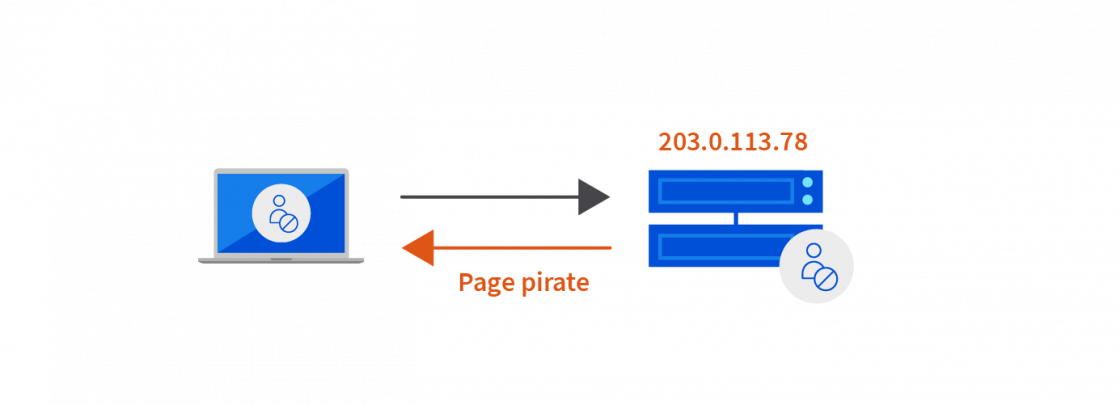
The browser uses this IP address to retrieve the website’s content. The spoofed server will then direct to a page that looks like www.ovhcloud.com so that the hacker can obtain the user’s personal information (phishing).
What is DNSSEC?
DNSSEC guarantees that a DNS response is authentic. When the browser sends a request, it receives an authentication key, certifying that the IP provided is correct.

An IP validated by DNSSEC therefore guarantees that the user will be granted access to the correct website. The goal is to uncover inconsistencies in the requests.
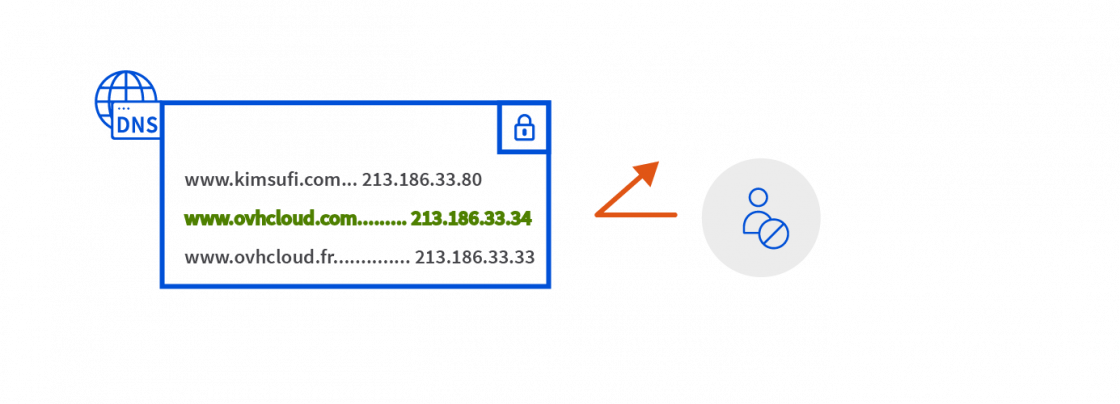
If a hacker tries to modify the table in a DNS server protected by DNSSEC, it will refuse the request, as the information supplied will not have been signed.
Your questions answered
How do I protect my DNS server?
To defend itself against this practice, the DNSSEC protocol uses the principles of asymmetric cryptography and digital signatures to guarantee the authenticity of the data, as well as proof of non-existence if the requested record does not exist and could be considered fraudulent.
What is a DNS used for?
A DNS server is used to obtain the IP address corresponding to a domain name (URL in the case of a website). It’s like a directory: the DNS service translates domain names into IP addresses and other types of records. The IP address is needed for your browser to contact the web server responsible for the site you want to visit, because the IP address uniquely identifies each machine connected to the Internet, just like a phone number. It is a discreet but crucial link for Internet security. The most common example of a DNS server is the BIND server, which is the most widely used on the internet.
Currently, IP addresses are mainly stored in IPv4 and a transition towards IPv6 addresses has begun. Each link between a domain name and an IP address is unique.
DNS servers have a hierarchy. The root (usually represented by a dot) is the highest hierarchical centre. You can then create several subdomains within a domain, which in turn can delegate subdomains hosted on other servers. Delegations then create areas with their own hierarchical system. The domains just below the root are the primary domains (TLDs or Top-Level Domains). Updates are made on the domain’s primary server. Zone transfer consists of the reproduction of primary server records by secondary servers.
What is a DNS lookup?
When a host searches for a domain, it repeatedly scans the entire DNS hierarchy until it finds the specific domain. An Internet service provider (ISP) provides recursive servers that perform these searches. When this server performs an IP address lookup, the server sends the request to the root servers. It will then choose one capable of providing a response. If that doesn’t happen, it will choose another server from the list, and so on. They may check several servers before finding the one that matches the request.
In the case of a reverse DNS resolution, i.e. a lookup using your IP address first, the search is done through a PTR input. This indicates the server host name that matches the relevant server address. If specified, it must contain the reverse record of a DNS A or AAAA record. Requests from online mail servers (emails, etc.) do not have a PTR record, so they are more likely to fail.
What are DNS server records?
For other DNS records, you will generally find the SOA (Start Of Authority) record, which provides information on the zone: primary server, contact email, different durations including expiration, zone serial number, and so on. It is like the identity card of the DNS server. This DNS data type record has a serial number that increases incrementally each time the zone file changes.
It also contains the TXT record, which allows an administrator to create text in a DNS record. Each record type comes with a TTL (Time to Live), i.e. how long the record is authorised to be stored in a cache server. This is where a DNS cache poisoning attack can occur.
What is cache poisoning?
DNS cache poisoning, or DNS spoofing, is a hacker technique that fools a DNS server into thinking that it has received a valid and authentic response to a request. The poisoned DNS server will cache the information. Users are then redirected to questionable websites, which can be used for phishing purposes or as a channel to install a virus.
Generally, the attacker exploits a vulnerability in the DNS server that would accept imprecise or false requests. The victims, who are expecting to see the website they wanted, are instead shown other potentially dangerous content.
Generally, a DNS server has a port 53. The maximum size of a response must be 512 bytes. If it exceeds this size, the query is returned on TCP port 53. However, this type of redirection is rare, as hosting providers restrict the ability to transfer DNS zones in this way.
How do I configure a DNSSEC zone on my DNS for a domain name hosted by OVHcloud?
Find all the information to enable DNSSEC in the guides below:
Edit my DNS zone
Configuring the DNS server